In diesem Tutorial zeige ich Ihnen, wie Sie einen zusätzlichen Domänencontroller konfigurieren, was eines der Hauptmerkmale von SAMBA 4 ist. Ich werde den vorhandenen Samba 4-Server aus meinem vorherigen Tutorial als primären Domänencontroller verwenden. Dieses Setup bietet ein gewisses Maß an Lastausgleich und Failover für AD-Dienste (Ldap-Schemas und DNS) und die Konfiguration ist wirklich einfach. Wir können diese Funktion auch verwenden, um die Umgebung zu vergrößern.
Ich werde einen vorhandenen Samba4-AD-Server und einen neuen zusätzlichen Server verwenden.
Hinweis:In meinem vorherigen Artikel habe ich aufgrund eines Konflikts in 192.168.1.190 als primären Domänencontroller verwendet ipaddress in meiner Laborumgebung habe ich sie in 192.168.1.180 geändert.
Server
- 192.168.1.180, samba4.sunil.cc – Primärer Domänencontroller Centos7 AD1
- 192.168.1.170,dc.sunil.cc – Sekundärer Domänencontroller oder zusätzlicher Domänencontroller Centos7 AD2
Wenn ich in der Anleitung bezeichne, dass sich AD1 auf den primären AD-Server und AD2 auf den sekundären Server bezieht, beziehen Sie sich bitte auf diesen Link.
Primären Domänencontroller konfigurieren
Bitte beachten Sie diesen Link
Samba 4 mit Active Directory auf CentOS 7 RPM-basierter Installation mit Share-Unterstützung
Sekundären Domänencontroller konfigurieren
AD2
Führen Sie auf dem Server 192.168.1.170, dc.sunil.cc - (Secondary Domain Controller oder Additional Domain Controller) Folgendes aus:
Wir werden Centos 7 als Basis verwenden, SELinux ist aktiviert.
[[email protected] ~]# yum -y update
Selinux ist aktiviert.
[[email protected] ~]# sestatus SELinux status: enabled SELinuxfs mount: /sys/fs/selinux SELinux root directory: /etc/selinux Loaded policy name: targeted Current mode: enforcing Mode from config file: enforcing Policy MLS status: enabled Policy deny_unknown status: allowed Max kernel policy version: 28 [[email protected] ~]#
Machen Sie einen Eintrag in der Hostdatei:
Achten Sie hier darauf, sowohl das primäre AD als auch das sekundäre AD in /etc/hosts
hinzuzufügenAD1
[[email protected] ~]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 192.168.1.180 samba4.sunil.cc samba4 192.168.1.170 dc.sunil.cc dc [[email protected] ~]#
AD2
[[email protected] ~]# cat /etc/hosts 127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 ::1 localhost localhost.localdomain localhost6 localhost6.localdomain6 192.168.1.180 samba4.sunil.cc samba4 192.168.1.170 dc.sunil.cc dc [[email protected] ~]#
Aktivieren Sie das epel-Repo.
[[email protected] ~]# yum install epel-release -y
Basispakete installieren.
[[email protected] ~]# yum install vim wget authconfig krb5-workstation -y
Installieren Sie das Wing-Repo für Samba4-RPMs.
[[email protected] ~]# cd /etc/yum.repos.d/ [[email protected] yum.repos.d]# wget http://wing-net.ddo.jp/wing/7/EL7.wing.repo [[email protected] yum.repos.d]# sed -i '[email protected][email protected][email protected]' /etc/yum.repos.d/EL7.wing.repo [[email protected] yum.repos.d]# yum clean all Loaded plugins: fastestmirror Cleaning repos: base extras updates wing wing-source Cleaning up everything Cleaning up list of fastest mirrors [[email protected] yum.repos.d]#
Installieren Sie jetzt die Samba4-Pakete.
[[email protected] yum.repos.d]# yum install -y samba45 samba45-winbind-clients samba45-winbind samba45-client\ samba45-dc samba45-pidl samba45-python samba45-winbind-krb5-locator perl-Parse-Yapp\ perl-Test-Base python2-crypto samba45-common-tools
Ändern Sie die resolv.conf , stellen Sie sicher, dass der Nameserver auf den primären Domänencontroller verweist, hier verwenden wir 192.168.1.180.
[[email protected] ~]# cat /etc/resolv.conf # Generated by NetworkManager search sunil.cc nameserver 192.168.1.180 [[email protected] ~]#
Jetzt entfernen wir diese Dateien, da wir sie später erstellen werden.
[[email protected] ~]# rm -rf /etc/krb5.conf [[email protected] ~]# rm -rf /etc/samba/smb.conf
Fügen Sie nun den folgenden Inhalt in krb5.conf hinzu, hier ist unser Domänenname sunil.cc, der Bereichsname ist SUNIL.CC.
[[email protected] ~]# cat /etc/krb5.conf
[libdefaults]
dns_lookup_realm = false
dns_lookup_kdc = true
default_realm = SUNIL.CC
[[email protected] ~]#
Überprüfen Sie, ob wir den Kerberos-Schlüssel vom Samba4-Server erhalten können.
[[email protected] ~]# kinit [email protected]
Password for [email protected]:
Warning: Your password will expire in 42 days on Sat 15 Jul 2017 10:54:19 PM CEST
[[email protected] ~]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: [email protected]
Valid starting Expires Service principal
06/03/2017 20:33:08 06/04/2017 06:33:08 krbtgt/[email protected]
renew until 06/04/2017 20:33:04
[[email protected] ~]#
Wenn Sie den Schlüssel nicht bekommen, vergewissern Sie sich, dass die Zeit synchron ist und überprüfen Sie bitte die resolv.conf.
Fügen Sie den Server jetzt der vorhandenen Domain hinzu.
[[email protected] yum.repos.d]# samba-tool domain join sunil.cc DC -U"SUNIL\administrator" --dns-backend=SAMBA_INTERNAL Finding a writeable DC for domain 'sunil.cc' Found DC samba4.sunil.cc Password for [SUNIL\administrator]: workgroup is SUNIL realm is sunil.cc Adding CN=DC,OU=Domain Controllers,DC=sunil,DC=cc Adding CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc Adding CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc Adding SPNs to CN=DC,OU=Domain Controllers,DC=sunil,DC=cc Setting account password for DC$ Enabling account Calling bare provision Looking up IPv4 addresses Looking up IPv6 addresses No IPv6 address will be assigned Setting up share.ldb Setting up secrets.ldb Setting up the registry Setting up the privileges database Setting up idmap db Setting up SAM db Setting up sam.ldb partitions and settings Setting up sam.ldb rootDSE Pre-loading the Samba 4 and AD schema A Kerberos configuration suitable for Samba 4 has been generated at /var/lib/samba/private/krb5.conf Provision OK for domain DN DC=sunil,DC=cc Starting replication Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[402/1550] linked_values[0/0] Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[804/1550] linked_values[0/0] Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[1206/1550] linked_values[0/0] Schema-DN[CN=Schema,CN=Configuration,DC=sunil,DC=cc] objects[1550/1550] linked_values[0/0] Analyze and apply schema objects Partition[CN=Configuration,DC=sunil,DC=cc] objects[402/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[804/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[1206/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[1608/1614] linked_values[0/0] Partition[CN=Configuration,DC=sunil,DC=cc] objects[1614/1614] linked_values[30/0] Replicating critical objects from the base DN of the domain Partition[DC=sunil,DC=cc] objects[97/97] linked_values[23/0] Partition[DC=sunil,DC=cc] objects[360/263] linked_values[23/0] Done with always replicated NC (base, config, schema) Replicating DC=DomainDnsZones,DC=sunil,DC=cc Partition[DC=DomainDnsZones,DC=sunil,DC=cc] objects[40/40] linked_values[0/0] Replicating DC=ForestDnsZones,DC=sunil,DC=cc Partition[DC=ForestDnsZones,DC=sunil,DC=cc] objects[18/18] linked_values[0/0] Committing SAM database Sending DsReplicaUpdateRefs for all the replicated partitions Setting isSynchronized and dsServiceName Setting up secrets database Joined domain SUNIL (SID S-1-5-21-2550466525-3862778800-1252273829) as a DC [[email protected] yum.repos.d]#
Fügen Sie die Firewall-Regeln hinzu.
[[email protected] ~]# firewall-cmd --add-port=53/tcp --permanent;firewall-cmd --add-port=53/udp --permanent;firewall-cmd --add-port=88/tcp --permanent;firewall-cmd --add-port=88/udp --permanent; \ firewall-cmd --add-port=135/tcp --permanent;firewall-cmd --add-port=137-138/udp --permanent;firewall-cmd --add-port=139/tcp --permanent; \ firewall-cmd --add-port=389/tcp --permanent;firewall-cmd --add-port=389/udp --permanent;firewall-cmd --add-port=445/tcp --permanent; \ firewall-cmd --add-port=464/tcp --permanent;firewall-cmd --add-port=464/udp --permanent;firewall-cmd --add-port=636/tcp --permanent; \ firewall-cmd --add-port=1024-3500/tcp --permanent;firewall-cmd --add-port=3268-3269/tcp --permanent [[email protected] ~]# firewall-cmd --reload
Fügen Sie nun das Startskript hinzu, da die Samba4-RPM von Wing es nicht hat.
[[email protected] ~]# cat /etc/systemd/system/samba.service [Unit] Description= Samba 4 Active Directory After=syslog.target After=network.target [Service] Type=forking PIDFile=/var/run/samba.pid ExecStart=/usr/sbin/samba [Install] WantedBy=multi-user.target [[email protected] ~]#
Samba 4 unterstützt derzeit keine Sysvol-Replikation, dies ist für Gruppen-GID-Zuordnungen erforderlich, hier ist die Problemumgehung, um dies zu beheben:
Muss die Sicherung von idmap.ldb aufnehmen und wiederherstellen.
DC1
Installieren Sie das Paket.
[[email protected] ~]#yum install tdb-tools
Hot-Backup erstellen.
[[email protected] ~]# tdbbackup -s .bak /var/lib/samba/private/idmap.ldb
Kopieren Sie die Sicherungsdatei auf DC2.
[[email protected] ~]# ls -l /var/lib/samba/private/idmap.ldb.bak -rw-------. 1 root root 61440 Jun 3 09:52 /var/lib/samba/private/idmap.ldb.bak [[email protected] ~]# scp -r /var/lib/samba/private/idmap.ldb.bak [email protected]:/var/lib/samba/private/idmap.ldb
DC2
Starten Sie jetzt den Samba-Dienst.
[[email protected] ~]# systemctl enable samba Created symlink from /etc/systemd/system/multi-user.target.wants/samba.service to /etc/systemd/system/samba.service. [[email protected] ~]# systemctl start samba
DC1
Ändern Sie die Datei resolv.conf so, dass sie auf 192.168.1.180 zeigt.
[[email protected] ~]# cat /etc/resolv.conf # Generated by NetworkManager search sunil.cc nameserver 192.168.1.180 [[email protected] ~]#
Link erstellen.
[[email protected] ~]# ln -s /var/lib/samba/private/krb5.conf /etc/krb5.conf
[[email protected] ~]# cat /etc/krb5.conf
[libdefaults]
default_realm = SUNIL.CC
dns_lookup_realm = false
dns_lookup_kdc = true
[[email protected] ~]#
Prüfe jetzt das Kerberos-Ticket.
[[email protected] ~]# kinit [email protected]
Password for [email protected]:
Warning: Your password will expire in 42 days on Sat 15 Jul 2017 10:54:19 PM CEST
[[email protected] ~]# klist
Ticket cache: FILE:/tmp/krb5cc_0
Default principal: [email protected]
Valid starting Expires Service principal
06/03/2017 22:03:07 06/04/2017 08:03:07 krbtgt/[email protected]
renew until 06/04/2017 22:03:03
[[email protected] ~]#
Jetzt ist unser zusätzlicher Domänencontroller bereit. Lassen Sie uns die Replikation überprüfen.
DC2
[[email protected] ~]# samba-tool drs showrepl
Default-First-Site-Name\DC
DSA Options: 0x00000001
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
DSA invocationId: e3f76609-f5f0-421d-99ad-38e1fba10b08
==== INBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ Sat Jun 3 22:37:24 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 22:37:24 2017 CEST
==== OUTBOUND NEIGHBORS ====
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\SAMBA4 via RPC
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 9a2b9a9c-064d-4de1-8c38-20072735de1c
Enabled : TRUE
Server DNS name : samba4.sunil.cc
Server DN name : CN=NTDS Settings,CN=SAMBA4,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
[[email protected] ~]#
DC1
Ausführen des gleichen Befehls.
[[email protected] private]# samba-tool drs showrepl
Default-First-Site-Name\SAMBA4
DSA Options: 0x00000001
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
DSA invocationId: 745838cd-21e5-4bea-aa28-400a21d59a83
==== INBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:48 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:53:49 2017 CEST failed, result 2 (WERR_BADFILE)
1 consecutive failure(s).
Last success @ NTTIME(0)
==== OUTBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:06 2017 CEST failed, result 2 (WERR_BADFILE)
3 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:06 2017 CEST failed, result 2 (WERR_BADFILE)
3 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:06 2017 CEST failed, result 2 (WERR_BADFILE)
3 consecutive failure(s).
Last success @ NTTIME(0)
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:02 2017 CEST failed, result 2 (WERR_BADFILE)
2 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 09:57:02 2017 CEST failed, result 2 (WERR_BADFILE)
2 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 9c5f7fe2-3cb7-4bb4-9f46-d2922a7a7ab4
Enabled : TRUE
Server DNS name : dc.sunil.cc
Server DN name : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
[[email protected] private]#
Wenn Sie diesen Fehler sehen, dann gibt es ein Problem mit der Replikation, wir müssen die Replikation erneut initiieren.
[[email protected] private]# samba-tool drs replicate samba4.sunil.cc dc.sunil.cc DC=sunil,DC=cc Replicate from dc.sunil.cc to samba4.sunil.cc was successful. [[email protected] private]#
Jetzt sollte die Replikation problemlos funktionieren.
[[email protected] private]# samba-tool drs showrepl
Default-First-Site-Name\SAMBA4
DSA Options: 0x00000001
DSA object GUID: cc0b412e-3bdc-4af7-95e8-90145425d40d
DSA invocationId: 745838cd-21e5-4bea-aa28-400a21d59a83
==== INBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ Sat Jun 3 10:42:04 2017 CEST was successful
0 consecutive failure(s).
Last success @ Sat Jun 3 10:42:04 2017 CEST
==== OUTBOUND NEIGHBORS ====
DC=ForestDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=DomainDnsZones,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Schema,CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
CN=Configuration,DC=sunil,DC=cc
Default-First-Site-Name\DC via RPC
DSA object GUID: 0b7607ae-0edc-4667-80f0-4c50bbdf742c
Last attempt @ NTTIME(0) was successful
0 consecutive failure(s).
Last success @ NTTIME(0)
==== KCC CONNECTION OBJECTS ====
Connection --
Connection name: 9c5f7fe2-3cb7-4bb4-9f46-d2922a7a7ab4
Enabled : TRUE
Server DNS name : dc.sunil.cc
Server DN name : CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Sites,CN=Configuration,DC=sunil,DC=cc
TransportType: RPC
options: 0x00000001
Warning: No NC replicated for Connection!
[[email protected] private]#
Testen Sie jetzt, ob die Objekte zwischen DC1 und DC2 repliziert werden.
Wir werden zuerst einen Testbenutzer in DC2 erstellen und sehen, ob der Benutzer in DC1 gesehen wird.
DC2
[[email protected] ~]# samba-tool user create howtoforge New Password: Retype Password: User 'howtoforge' created successfully [[email protected] ~]# samba-tool user list Administrator howtoforge test_user1 test_user krbtgt Guest [[email protected] ~]#
Überprüfen Sie jetzt dasselbe von DC1.
DC1
[[email protected] ~]# samba-tool user list Administrator howtoforge test_user1 test_user krbtgt Guest [[email protected] ~]#
Lassen Sie uns nun die DNS-Replikation überprüfen.
Ich werde denselben Windows 10-Client verwenden, den ich in meinem vorherigen Tutorial Samba4-Domänencontroller-Installation aus der Quelle verwendet habe.
192.168.1.191 Fernverwaltung Win 10.
Fügt den AD2-Server als sekundären DNS hinzu.
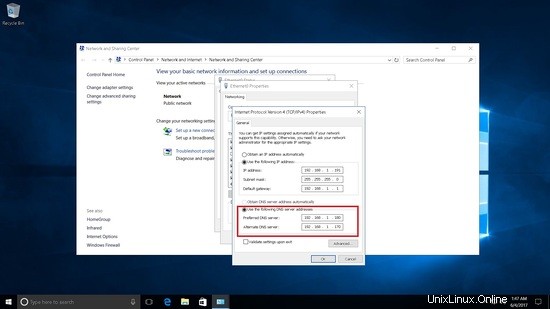
Testen der DNS-Replikation.
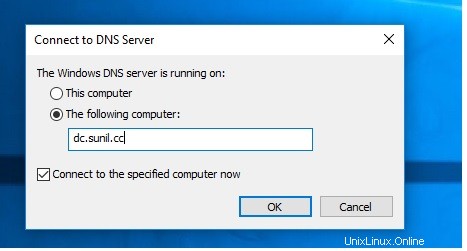
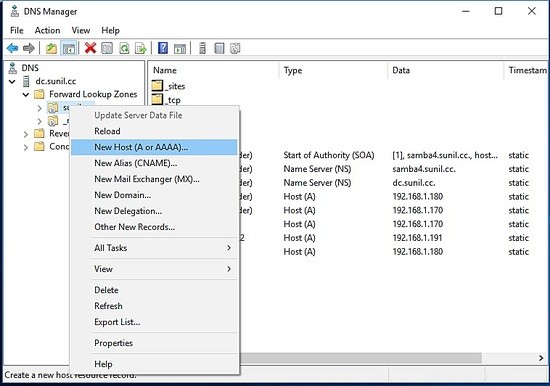
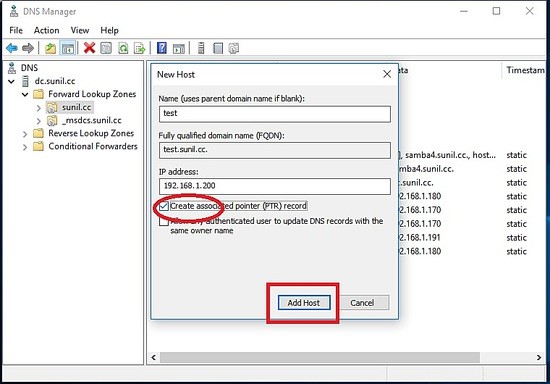
Überprüfen Sie die Namensauflösung.
[[email protected] ~]# nslookup test.sunil.cc 192.168.1.170 Server: 192.168.1.170 Address: 192.168.1.170#53 Name: test.sunil.cc Address: 192.168.1.200 [[email protected] ~]# nslookup test.sunil.cc 192.168.1.180 Server: 192.168.1.180 Address: 192.168.1.180#53 Name: test.sunil.cc Address: 192.168.1.200 [[email protected] ~]#
So funktionieren DNS und Replikation in Samba 4.